Fern Wifi Cracker Osx
Fern Wifi Cracker Fern WiFi Cracker is a python based tool that can be used for WEP/WPA/WPA2 cracking, session hijacking, ARP request replays, and performing brute force attacks. It is able to save the key in the database on a. Fern WIFI cracker. Disclaimer: I carried out this attack using my own WIFI network, all MAC Addresses and names have been faked. This tutorial is for learning purposes only and should not be used for any illegal activities. Introduction: This is a step by step on how to use the Fern WIFI Cracker that comes installed with Kali-Linux. Richardsonlima / Cracking WPA2 WEP Wifi Aircrack 10 seconds guide For Mac OSX Sierra. Last active Dec 4, 2020.
| '' |
| Fern-Wifi-Cracker 2.0 Not working with Ralink Chipsets (tested on AWUS036NH ) |
| What steps will reproduce the problem? |
| 1.start fern-wifi |
| 2.select interface |
| What is the expected output? What do you see instead? |
| expected output: 'Monitor mode enabled on wlan0mon' |
| instead: stuck in set_monitor_thread() |
| What version of the product are you using? On what operating system? |
| Linux Mint 64: |
| Linux xxxxxxxx 3.13.0-24-generic #47-Ubuntu SMP Fri May 2 23:30:00 UTC 2014 x86_64 x86_64 x86_64 GNU/Linux |
| Please provide any additional information below. |
| the reason: you only search for monitors with *mon pattern |
| realtek chipsets and recent airmon-ng version use a new pattern: wlandmon |
| here is a bugfix, i use for my version: |
| '' |
| defset_monitor_thread(self,monitor_card,mac_setting_exists,last_settings): |
| #print 'starting new thread' |
| status=str(commands.getoutput('airmon-ng start %s'%(monitor_card))) |
| #print 'nStatus of airmon-ng start', monitor_card, ':', status,'n' |
| if ('monitor mode enabled'instatus) or ('monitor mode vif enabled'instatus): #fix for ralink if |
| monitor_interface_process=str(commands.getoutput('airmon-ng')) |
| #print 'monitor_interface_process:', monitor_interface_process, 'n' |
| if ('monitor mode enabled'instatus): |
| regex=re.compile('mond',re.IGNORECASE) |
| elif ('monitor mode vif enabled'instatus): |
| regex=re.compile('wlandmon',re.IGNORECASE) #changed from mond to wlandmon |
| interfaces=regex.findall(monitor_interface_process) |
| print'available interfaces:', interfaces |
| if(interfaces): |
| self.monitor_interface=interfaces[0] |
| else: |
| self.monitor_interface=monitor_card |
| print'setting self.monitor_interface to', self.monitor_interface |
| variables.monitor_interface=self.monitor_interface |
| self.interface_combo.setEnabled(False) |
| variables.wps_functions.monitor_interface=self.monitor_interface |
| self.emit(QtCore.SIGNAL('monitor mode enabled')) |
| # Create Fake Mac Address and index for use |
| mon_down=commands.getstatusoutput('ifconfig %s down'%(self.monitor_interface)) |
| ifmac_setting_exists: |
| variables.exec_command('macchanger -m %s %s'%(last_settings,self.monitor_interface)) |
| else: |
| variables.exec_command('macchanger -A %s'%(self.monitor_interface)) |
| mon_up=commands.getstatusoutput('ifconfig %s up'%(self.monitor_interface)) |
| foriterateinos.listdir('/sys/class/net'): |
| ifstr(iterate) str(self.monitor_interface): |
| os.chmod('/sys/class/net/'+self.monitor_interface+'/address',0777) |
| variables.monitor_mac_address=reader('/sys/class/net/'+self.monitor_interface+'/address').strip() |
| variables.wps_functions.monitor_mac_address=variables.monitor_mac_address |
| else: |
| print'problem occured while setting up the monitor mode of selected', monitor_card |
commented Jan 4, 2015
now intergrated in Fern-Wifi-Cracker 2.1 ( https://code.google.com/p/fern-wifi-cracker/issues/detail?id=97 ) |
commented Jan 21, 2015

Hello, I use Kali Linux in VMware Fusion (Mac OS X). When i choose the wlan0 (AWUSO36NH) on fern-wifi, a problem appears ... I'm trying to attack and WPA access. So i think Fern-Wifi Cracker doesn't work well with AWUS036NH. Sorry for my poor english. |
Wifi Hacking is the most trending activity nowadays. You have a good and active internet connection at your home, still, you want to connect with your neighbor’s wireless system for getting free internet.

Fern Wifi Cracker Mac Address
If you are one of them and want to hack neighbor’s wifi or willing to access free internet through wifi access point listed in your device.
You should not forget that your neighbor is searching for the same activity. If you have wifi access point at your home or office, then a bad man sitting behind you will try to hack your wifi.
Your first task Secure your wifi network before trying to hack nearby wireless access points. Here you can go 5 Tips, How to secure wifi from hacking If you will follow these tips no one can hack into your wifi easily.
What are the wifi hacking tools used by a hacker to hack into wifi? I think this question is revolving your head. This article will help you to find out this software.
Fern Wifi Cracker Mac Download
Are you looking for wifi Hacking Software?
If yes, this post is useful for you. I will provide description and download links of tools used for wifi hacking. Here you will go to get information about the software.
Aircrack-ng
Aircrack-ng is a most popular wifi hacking software used to crack WEP, WPA/WPA2, and WPS. Sometimes hackers use to crack the security of wifi radius server too. Aircrack-ng is a bundle of multiple tools such as airmon-ng, airodump-ng, aireplay-ng etc. if you don’t know how to use this tool, then visit official website of aircrack-ng website http://www.aircrack-ng.org/
Home Page
Wifite
This is an awesome tool, you can perform multiple attacks, WEP, WPA/WPA2, WPS in a row. Wifite aims to be the “set it and forget it” wireless auditing tool.Features:
- sorts targets by signal strength (in dB); cracks closest access points first
- automatically de-authenticates clients of hidden networks to reveal SSIDs
- numerous filters to specify exactly what to attack (WEP/WPA/both, above certain signal strengths, channels, etc)
- customizable settings (timeouts, packets/sec, etc)
- “anonymous” feature; changes MAC to a random address before attacking, then changes back when attacks are complete
- all captured WPA handshakes are backed up to wifite.py’s current directory
- smart WPA de-authentication; cycles between all clients and broadcast deauths
- stop any attack with Ctrl+C, with options to continue, move onto next target, skip to cracking, or exit
- displays session summary at exit; shows any cracked keys
- all passwords saved to cracked.txt
Wifite Home Page
Reaver
Reaver wifi hacking software for Linux. Reaver performs brute force against WPS ( Wifi Protected Setup). In this setup, a pin number is required to connect wifi no matter what security is implemented WEP or WPA/WPA2. It can get password both. In normal condition, Reaver will recover password against Wpa/wpa2 within 4-8 hours, depending on AP.
Reaver Home Page
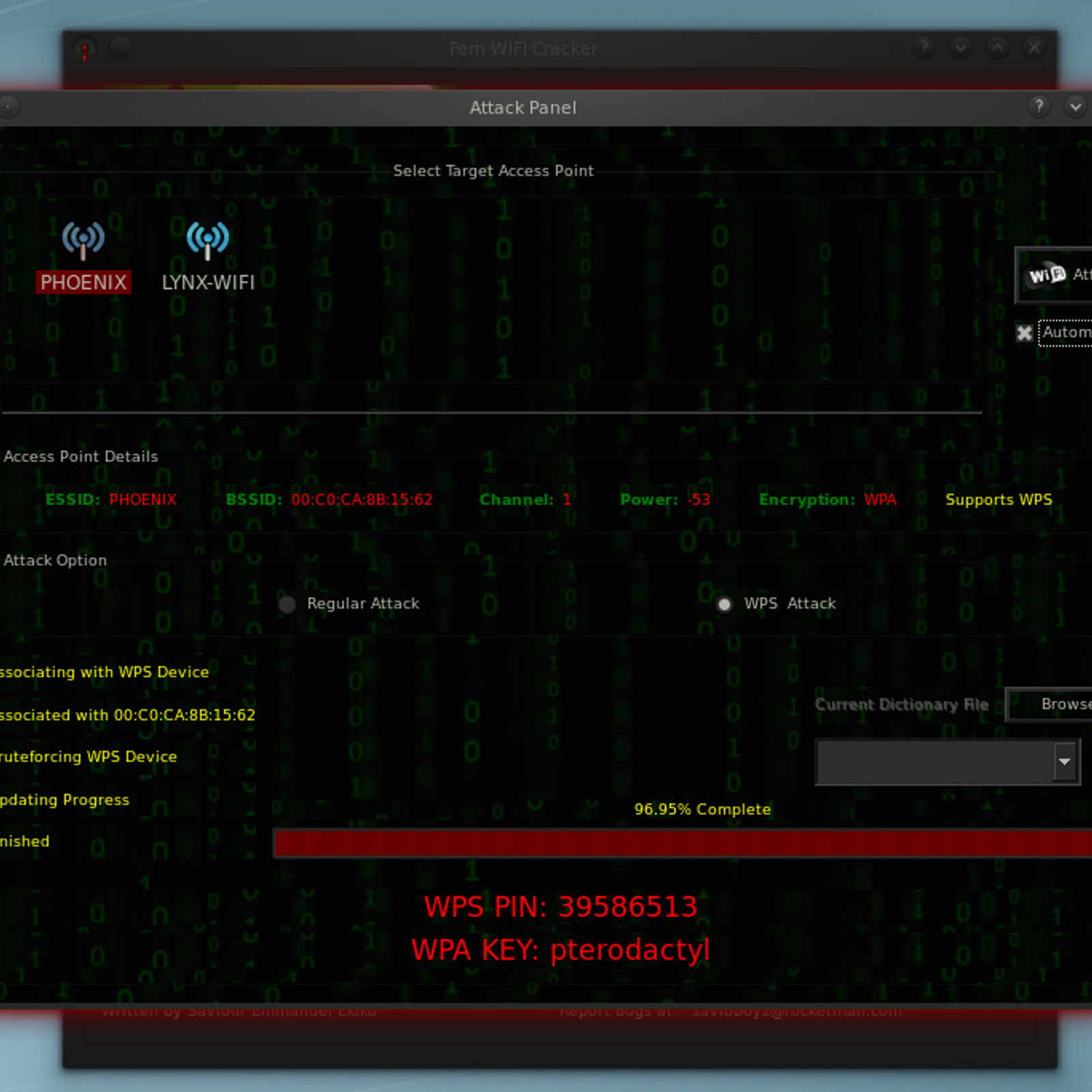
Fern Wifi Cracker
If you love GUI interface, you will love this wifi hacking tool. because it has GUI. It helps to crack WEP, WPA/WPA2 & WPS security. It has lots of other features like MITM, sniffing, Session hijacking etc.Features:
- WEP Cracking with Fragmentation,Chop-Chop, Caffe-Latte, Hirte, ARP Request Replay or WPS attack
- WPA/WPA2 Cracking with Dictionary or WPS based attacks
- Automatic saving of key in database on successful crack
- Automatic Access Point Attack System
- Session Hijacking (Passive and Ethernet Modes)
- Access Point MAC Address Geo Location Tracking
- Internal MITM Engine
- Bruteforce Attacks (HTTP,HTTPS,TELNET,FTP)
- Update Support
Fern Wifi Cracker Home Page
PixieWPS
PixieWPS is very simple and effective tool use to crack WPS security.
Features:- Checksum optimization: it’ll try first for valid PINs (11’000);
- Reduced entropy of the seed from 32 to 25 bits for the C LCG pseudo-random function;
- Small Diffie-Hellman keys: don’t need to specify the Public Registrar Key if the same option is used with Reaver.
Home Page
Fern Wifi Cracker Tutorial
MODULE 14:- WiFi Hacking and Security
If Appreciate My Work, You should consider:
Fern Wifi Cracker Github
- Join Group for Discussion Facebook Group
- Get your own self-hosted blog with a Free Domain at ($2.96/month)
- Buy a Coffee to Us! Make Small Contribution by Paypal
- Support us by taking our :Online Courses
- Contact me :[email protected]